Message Path Model
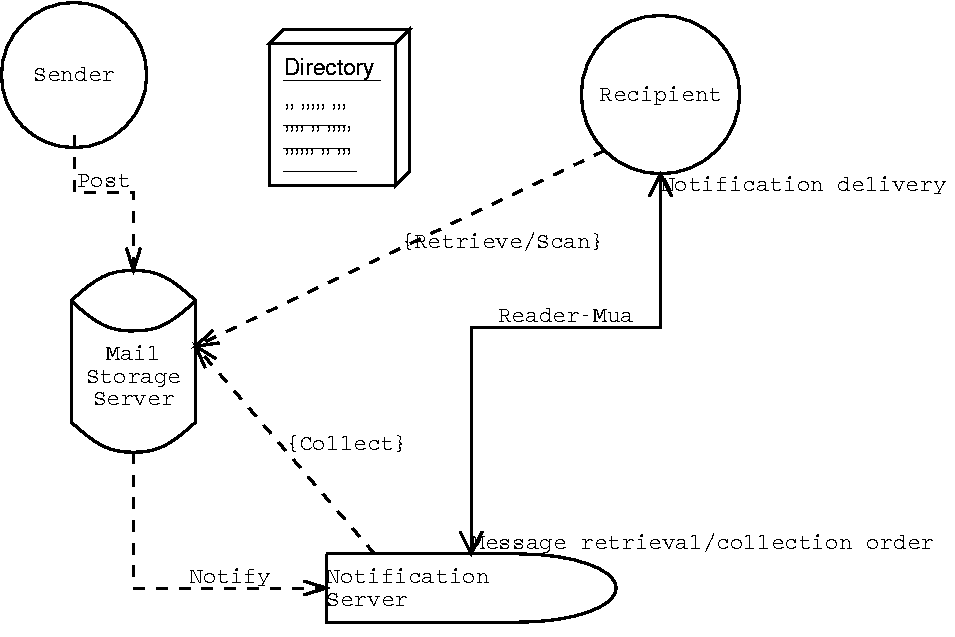
In figure * we can see the sender and receiver
drawn as circles. These are to be interpreted either as Mail-"user"-identities
on the respective servers (Mail storage and Notification), or as computers
or programs which act upon the respective identities, as is the case
for example with dial-up conected PC's, or mailing robots.
The lines represent a "protocol" which realizes the corresponding
activity
- Post:
- a Sender deposits a message for zero, one or more recipients
on the Mail Storage Server.
- Notify:
- a mail storage server creates notification messages to each
recipient (if any). There can be zero, one or more notification messages,
in dependence of the intended message interchange.
- (Notification) delivery:
- upon receipt of a Notification message
the Notification Servers takes action to make the intended Recipient
eventually know of the existence of a message posted to its identity.
The notification message may be discarded upon certain criteria without
notification delivery, it may be stored until somebody scans the Notification
Server for "new messages", or it can trigger an imediate action.
- (Message) collection order:
- a Notification Server can be instructed
by a Recipient to retrieve messages, selected out of the list of Notifications
available for this Recipient, eventually matching criteria defined
by the Recipient or by the owner of the Server.
- Collect:
- a Notification Server can contact a Mail Storage Server
to retrieve a posted message asociated with a certain Notification
Message. After acomplishing this step, the Message is copied over
to the Notification Server.
Optionally the Notification Server can collect messages in advance
without a collection order.
The collection includes eventually selection of messages with predefined
criteria about contents or meta-data (Sender, Mail Storage Server,
transport or protocol confiability) defined by the Recipient (inclusive/exclusive)
or by the owner of the Server (exclusive). (Notes in parentesis =
recomended behaviour).
- (Message) retrieval order:
- a Notification Server can be instructed
to hand out messages to the Recipient.
- Retrieve:
- a Recipient can initiate a message retrieval operation
directly. This implies a conection to the Mail Storage Server which
holds the message, and copy the message from there to the local computer
- be it the Notification Server or any Workstation the Recipient is
using.
This is an optional function.
- Scan:
- a Recipient can scan a certain Mail Storage Server for publically
available Messages, or for Messages posted for the Recipient itself.
This is an optional function.
- Sender, Recipient:
- are virtual identities, which can be
originators or recipients of messages. They can be asociated with
human beeings, with mail robots (computer programs) or with client
computers, accessing Storage or Notification Servers upon a Sender/Recipient
identy.
- (Mail/Message) Storage Server:
- Is a computer (host) which allows
certain Senders to deposit a message dedicated to zero one or more
Recipients. The asociation of a particular Sender with a particular
Storage Server can be verified at any time via a Directory Service
that is not part of the message path.
The Storage Server provides physical storage room for the message,
and means to notify the recipient - eventually repetedly, to autentify
collect and retrieve attempts and to deliver messages.
- Notification Server:
- Is a computer (host) which is dedicated to
reception of Notification Messages to certain Recipients. The asociation
of a particular Recipient with a Notification Server can be verified
at any time via a Directory Service that is not part of the message
path.
- Directory:
- Is a means by which an Actor can proove to a known extent
of trust the asociation of a virtual identity with a Message
or with another Actor.
Known extent of trust means, that an Actor can take decisions based
on the source of information - the particular Directory.
More profane: a Directory can be a local Blacklist or Whitelist, a
keyserver, a username lookup, a "real" directory service like
LDAP, and even an arbitrary piece of information, like the Return
Address of a traditional Email.
Georg Lehner - homepage









